
I vividly remember the moment the water main burst on our street when I was a kid; a spectacular geyser raising to the height of the second floor windows and us, the kids, gleefully enjoying a mini catastrophe that left the whole city block without water for a couple of days. This is the image that kept coming back to me while reading "ReCon: Revealing and Controlling PII Leaks in Mobile Network Traffic". The paper details the efforts of a team of computer science researchers at Northeastern University Boston to design a cross-platform system that reveals PII (personal information) leaks and gives users control over them in a very straightforward way.
The reason? In the words of the authors: because apps running on mobile devices "extensively track and leak users’ personally identifiable information (PII)". While a lot of such data sharing is completely legitimate, the authors argue that users have little visibility into what gets leaked and poor control over how, when and where that traffic is sent and handled by third parties.
How bad is the leakage of personally identifiable data?
David Choffnes, assistant Professor in the College of Computer and Information Science at Northeastern University, investigated how well user privacy is protected on a number of online services (app or web-based) by looking at the what types of user data apps or websites share with or leak to third parties. Some types of data most of us do not mind being shared (e.g. device type), but by the same token we cringe when we learn that our full name, location, birthday or even id and password being sent to the advertisers and data analytics companies.
Let me show you a couple of examples taken from their App vs Web leakage web page: as you can see from the screencaptures below, I have indicated my privacy preferences and have selected Android as my mobile OS. Accuweather gives you more more privacy on the app, whereas Amazon Shopping is definitely to be enjoyed on the web if you care about where your personal data end up.
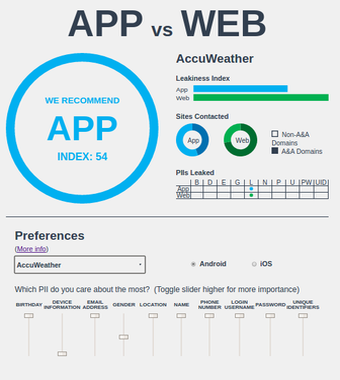
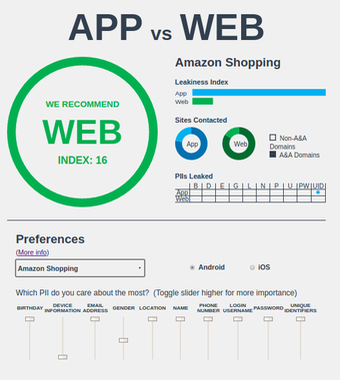
What exactly gets leaked?
You can check here the ReCon custom leakiness score (a weighted sum of the type of PII leaked, the amount of times leaked, and the number of domains it is leaked to). Behavior such as sending your password in plaintext (which exposes it to potential hackers) is given very high weight and will appear near the top.
Below I list a couple of examples (just for Android, but the same holds true for iOS) ranging from chilling to just bothersome. I’ve tried to pick the most representative examples (but feel free to explore the list for yourself and draw your own conclusions):
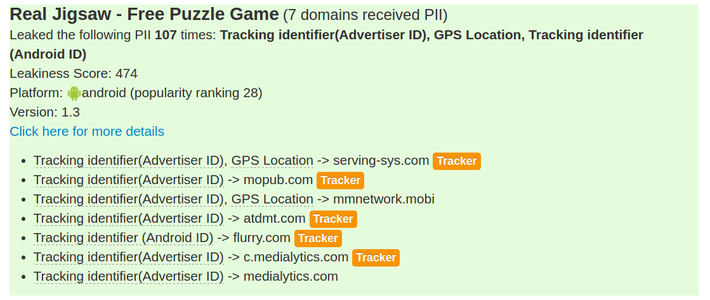
Or
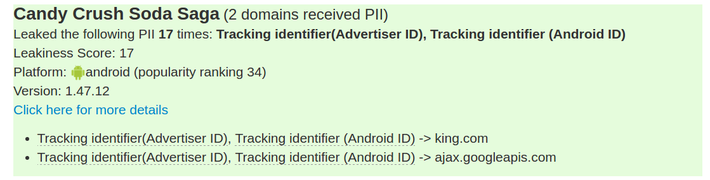
Or
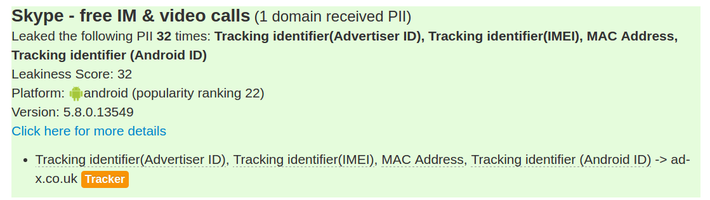
A lot of PII is leaked in plaintext, potentially easily intercepted
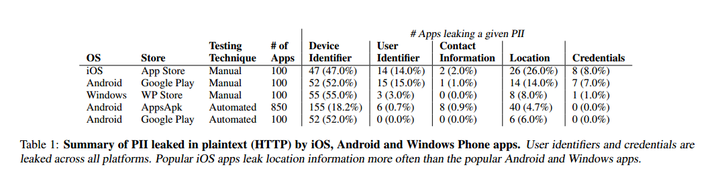
Here a table from the article I mentioned at the beginning of the post, that sums up nicely just how widespread is PII leakage in plaintext:
Where is ke Solutions on privacy protection?
It is impossible to work in web & app development without having a pretty good idea that user privacy is important. Right from the beginning we have implemented a set of internal policies that has proved its usefulness over the years:
- We do not send data of any kind to third parties (with the sole exception of Google Analytics tracker)
- Where we implemented shopping it was secured and encrypted
- Full transparency
- We are PCI compliant
Our web and app design and development solutions are oriented towards our customers. We have high standards which focus on efficiency, simplicity and appeal. Our clients get highly functional, user friendly and search engine friendly websites and apps.

Experience. Accomplishment.
Great Results





Posting comment as guest.
If you already have an account, please LOGIN.
If not, you may consider creating on. It’s FREE!